ThetaPoint’s Security Reference Architecture (SRA) is a Framework to organize all the components (People, Process, and Technology) to establish successful Security Operations (SecOps). The openness of the SRA allows organizations to take control of their SecOps: Establish Roles and Responsibilities, Establish Repeatable Processes, Control Costs, Vendor Independence, Modernization of Legacy Technologies, and Adoption of Technologies not supported by current Vendors.
Download ThetaPoint’s Security Reference Architecture (SRA) Solution Brief.
People
As detailed in our SRA – People Blog Post, many organizations struggle identifying, hiring, and retaining qualified security personnel. Because of this challenge, we often see organizations reducing their standards, leading to individuals who are ill-suited for their responsibilities or trapped with no opportunity for career progression. Because so many organizations are seeking the same types of skillsets, adding too many requirements to the position can limit your search. In addition, promoting from within and from the wrong skillsets can pigeonhole you and your staff for years to come. In some scenarios, your talent pool can become insufficient and unbalanced: heavy in some skill areas, light in others, and lacking critical skills for organizational success.
As part of our SOC Optimization Services we focus on a couple of key organizational aspects to build a successful SOC framework for your most valuable resource, your People. As part of this framework, we establish a proper Organization Chart, Mission and Charter, Roles and Responsibilities, and the requisite knowledge, skills, and abilities your team will need to support each staff position. We will also establish a clear path for talent development and career progression within each role and how that will play into your strategy for managing churn.
Sample Roles and Responsibilities (Not Exhaustive)

Process
As detailed in our SRA – Process Blog Post, repeatable processes create consistent outcomes – for better or worse. Defects in those processes can cause flawed investigations, system outages, and missed incidents. Your SOC produces its most valuable data from human judgement. However, this value comes from uniformity and reliability. The effects of poor processes ripple outward to distort incident reviews, assessments, and forecasts. Processes that do not capture the right data at the right time risk validity under future scrutiny. Looking back on your process data is always difficult, but it’s even harder when you don’t have the right data to look at.
As part of our SOC Optimization Services we focus on establishing a process life-cycle that fits within your organization’s internal controls to create repeatable and positive outcomes. If your organization does not have an accommodating internal controls process, then you can manage your SOC processes as though they were any software development or IT implementation project that needs regular refreshes. If you regularly reassess the value of your work through the lens of the goals above, you can prevent those “What were we thinking?” and “Why are we doing this?” moments.
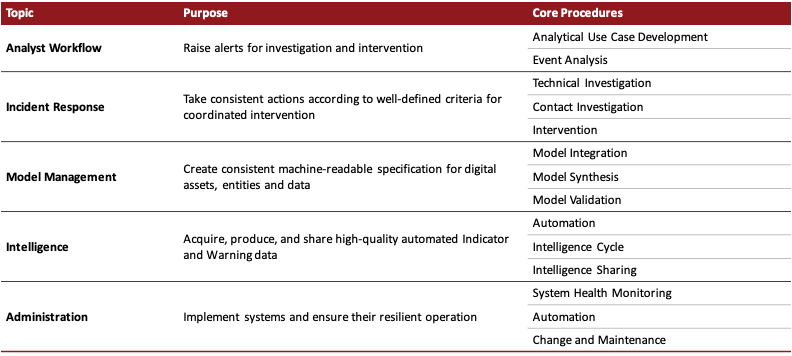
Sample Process and Procedures (Not Exhaustive)
Technology
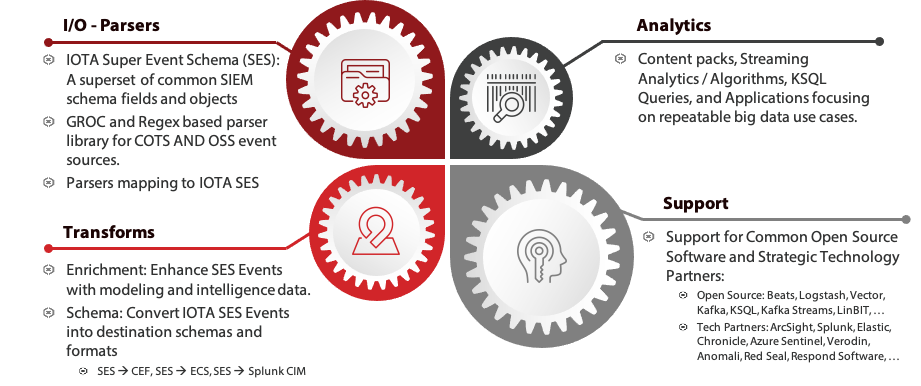
As detailed in the SRA – Technology Blog Post, Technology should always cater to business requirements rather than force users to adapt to the technology. ThetaPoint architects a model into a separate repository that has its own SOC-supporting features and governance. Organizations often have many different product silos that must be considered when instituting security monitoring controls. ThetaPoint takes this issue into consideration by producing a model, which we call IOTA, that allows for the ingest of any data, utilizes this data to massage and enrich it, and then allows for systems to execute automated actions on an analyst’s behalf.
ThetaPoint’s Security Reference Architecture has abstracted the Security Operations Center’s (SOC) technology stack into four simple buckets: Input, Output, Transform, and Analyze (IOTA). First, we recognize that ALL SIEM / Log Management / Big Data Technologies have similar primary features, functionality, and/or characteristics that fit into one of 4 buckets…

Next, we identify competing and complementary products / vendors and determine the features and functionalities they primarily support in a SecOps environment. These categories focus on the critical services that the SOC performs. Many proprietary tools provide more than one of these services, but since vendor independence is one of our overarching goals, this division allows us to focus on the key features needed to support our production use cases. This simplified stack helps frame discussions about organizational responsibilities in the context of supporting the SOC as well as how the SOC can leverage parts of the enterprise technology stack to meet its mission.

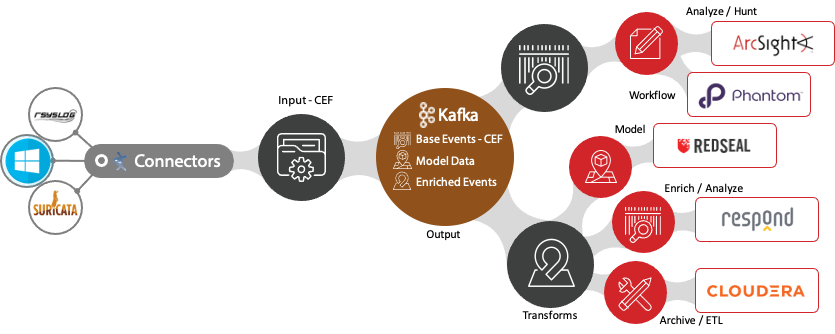
Finally, we adopt a Centralized Message Bus (Kafka), which is necessary to allow all the Technologies in your SecOps environment the ability to communicate with each other in a cohesive manner. This technology platform allows applications to publish and subscribe to a high throughput, low latency and fault tolerant message bus to insure events are delivered and received accordingly. As we bring everything together, we can see IOTA in Action by displaying a sample IOTA Architecture that focuses on modernizing a legacy ArcSight implementation while adding complementary technology into a cohesive SecOps architecture.
IOTA Toolkit (Beta)
As part of our technical Solutions and Services, ThetaPoint uses the Reference Architecture to help clients establish a repeatable and scalable framework to extend SOC capabilities, reduce Total Cost of Ownership (TCO), take ownership of their data, reduce dependence on costly software, and adopt emerging technologies that help address current real-world problems. We understand that implementing an SRA Environment can be a daunting task. That is why ThetaPoint provides a Full Resource Library called IOTA Toolkit (Beta) to help organizations Build, Maintain, Optimize, and Support a SRA Compatible Environment.