Security Optimization Services
ThetaPoint’s Security Optimization Service is based on our expertise in security architecture, administration, monitoring, incident response, and operation centers. Leveraging the ThetaPoint Security Reference Architecture, we begin by conducting a SOC Workshop that focuses primarily on People and Process. The results of the workshop will establish a SOC roadmap that will direct key operational decisions.
SOC Optimization Workshop
Technology is one aspect of an effective IT security or incident response program, not a magic elixir that will cure all that ails them. Organizations must also have business goals, a strategy on how to use the technology, the right people in place, and defined processes and procedures to enable their operations to be successful. ThetaPoint’s SOC Workshop focuses on the supporting infrastructure of Security Operations (SecOps). The goal of the workshop is to provide clients with an understanding of all the variables in their environment that need to be in place to support SecOps and establish a Roadmap for Success.
SOC Strategy and Roadmap
- Do you have a document that states your department’s vision? Mission and charter? Department SWOT analysis? How about your team’s 6 month-1 year-2 year strategy and roadmap for how you will execute on your functions? A plan on delivering meaningful statistics and metrics?
- Every organization should have these in a document or set of documents and IT Security Operations (SecOps) groups are no different.
- Without having these documents clearly defined and documented, the department is haphazardly going through the motions of looking “busy” but likely going nowhere specific, fast.
- ThetaPoint will work with our clients to build out department/team/division level roadmaps for their people, processes, and technology to support and mature the Security Operations functions to which they are responsible. This typically comes from working with department management and leaders in an off-site type of meeting environment.
SOC SWOT Analysis
IT Security Operations Centers (SOC) are only as good as their ability to monitor, detect, respond, and predict – all of which should align to the desired outcomes and metrics set by the company leaders. SOCs are an intricate mix of people, processes and technology executing on a select set of mission parameters to protect the company to which they are chartered.
SWOT Assessments help you get an understanding of:
1. The current maturity level of your SOC and what to do to up your game.
2. Skills needed in the security analyst roles to perform their important functions.
3. Required workflows to execute your chartered mission (e.g. incident response, change management, day-to-day operations, etc).
4. Necessary processes & procedures required to run an efficient and effective SOC.
5. The right tools & technology to leverage in order to perform the SOC’s mission.
A Focus on People
As detailed in our SRA – People Blog Post, many organizations struggle identifying, hiring, and retaining qualified security personnel. Because of this challenge, we often see organizations reducing their standards, leading to individuals who are ill-suited for their responsibilities or trapped with no opportunity for career progression. Because so many organizations are seeking the same types of skillsets, adding too many requirements to the position can limit your search. In addition, promoting from within and from the wrong skillsets can pigeonhole you and your staff for years to come. In some scenarios, your talent pool can become insufficient and unbalanced: heavy in some skill areas, light in others, and lacking critical skills for organizational success.
As part of our SOC Workshop we focus on a couple of key organizational aspects to build a successful SOC framework for your most valuable resource, your People. As part of this framework, we establish a proper Organization Chart, Mission and Charter, Roles and Responsibilities, and the requisite knowledge, skills, and abilities your team will need to support each staff position. We will also establish a clear path for talent development and career progression within each role and how that will play into your strategy for managing churn.
Sample Roles and Responsibilities (Not Exhaustive)

A Focus on Process
As detailed in our SRA – Process Blog Post, repeatable processes create consistent outcomes – for better or worse. Defects in those processes can cause flawed investigations, system outages, and missed incidents. Your SOC produces its most valuable data from human judgement. However, this value comes from uniformity and reliability. The effects of poor processes ripple outward to distort incident reviews, assessments, and forecasts. Processes that do not capture the right data at the right time risk validity under future scrutiny. Looking back on your process data is always difficult, but it’s even harder when you don’t have the right data to look at.
As part of our SOC Workshop we focus on establishing a process life-cycle that fits within your organization’s internal controls to create repeatable and positive outcomes. If your organization does not have an accommodating internal controls process, then you can manage your SOC processes as though they were any software development or IT implementation project that needs regular refreshes. If you regularly reassess the value of your work through the lens of the goals above, you can prevent those “What were we thinking?” and “Why are we doing this?” moments.
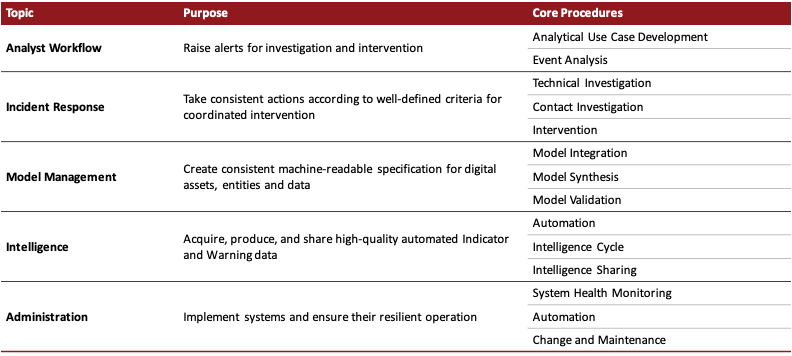
Sample Process and Procedures (Not Exhaustive)
Added Value SOC Services
Upon completion of the SOC Workshop, clients will have an established understanding of their strengths and weaknesses as it relates to their People. The next step is to implement the Workshop’s Roadmap to ensure that all roles and responsibilities have been adequately staffed by knowledgeable people.
It is not always feasible for organizations to be able to staff all resources with internal employees. ThetaPoint’s Staff Augmentation Service provides clients with world class engineers, analysts, and support staff. ThetaPoint can provide individual resources to fill gaps or assist clients through our Managed Services for SOC Engineers and SOC Analysts.
Upon completion of the SOC Workshop, clients will have an established understanding of their strengths and weaknesses as it relates to Policy and Procedures. The next step is to implement the Workshop’s Roadmap to ensure uniformity, reliability, and consistency across all workflows and processes.
ThetaPoint’s Policy and Procedure Development service assists clients in development activities by using proven policy and procedures as a baseline, then customizing to meet the organization’s business needs.